Section Navigation
Thareja Infrastructure Services
As businesses undergo digital transformation, the need for a robust and scalable IT infrastructure becomes paramount. Modern enterprise technologies demand infrastructure that delivers the computing power, storage, connectivity, and security necessary to support advanced applications and services. Without the right infrastructure in place, organizations may struggle to fully leverage the benefits of digital transformation, including efficiency gains, innovation, and enhanced customer experiences.
At Thareja, we understand the critical role that infrastructure plays in enabling organizations to meet their business goals. Our comprehensive infrastructure services are designed to help businesses upgrade, redesign, and manage their IT environments, ensuring they are equipped to handle today’s demands and tomorrow’s challenges.
Why Choose Thareja for Infrastructure Services?
Thareja is the ideal partner for managing and modernizing enterprise infrastructure. We bring the following qualifications to every engagement:
- Highly Skilled Team: Thareja has a large team of certified and qualified infrastructure professionals with expertise in a wide array of technologies, ensuring that your systems are managed by experts who understand the nuances of your business needs.
- Extensive Experience: With more than 35 enterprise infrastructure management engagements ongoing, we have a deep understanding of the unique requirements across industries and sectors. From public sector clients to private enterprises, we bring industry-specific knowledge to deliver tailored solutions.
- Global Reach: With more than 35 enterprise infrastructure management engagements ongoing, we have a deep understanding of the unique requirements across industries and sectors. From public sector clients to private enterprises, we bring industry-specific knowledge to deliver tailored solutions.
- Complex System Expertise: From simple infrastructure setups to complex systems capable of processing over 1 billion transactions per day, Thareja has the expertise to handle infrastructure projects of any scale. Whether it’s upgrading existing systems or building new ones from the ground up, we ensure your infrastructure performs at optimal levels.
- Certified Processes for Quality and Security: Thareja processes and procedures are ISO certified, including ISO 9001:2015 (Quality Management), ISO 27001:2013 (Information Security Management), and ISO 20000:2018 (Service Management). We are also CMMI Level 5 (Development) certified, reflecting our commitment to delivering the highest levels of service and quality assurance.
- 24/7/365 Support: Modern businesses operate around the clock, and so do we. Thareja provides 24/7/365 support, ensuring that your infrastructure is monitored and managed continuously, with rapid response times to minimize downtime and disruptions.
- Flexible Engagement Models: Every business has unique needs and budgets, and Thareja offers flexible engagement models to cater to your preferences. Whether you require full-time management, project-based support, or hybrid models, we work within your constraints to deliver optimal results.
- Seamless Digital Transformation Services: In addition to infrastructure management, Thareja offers a full range of digital transformation services, including cloud migration, AI integration, and automation. We ensure that your infrastructure aligns with your broader digital goals and can scale to meet future demands.
Full Range of Infrastructure Services
Thareja offers a comprehensive suite of infrastructure services designed to optimize performance, enhance security, and reduce costs.
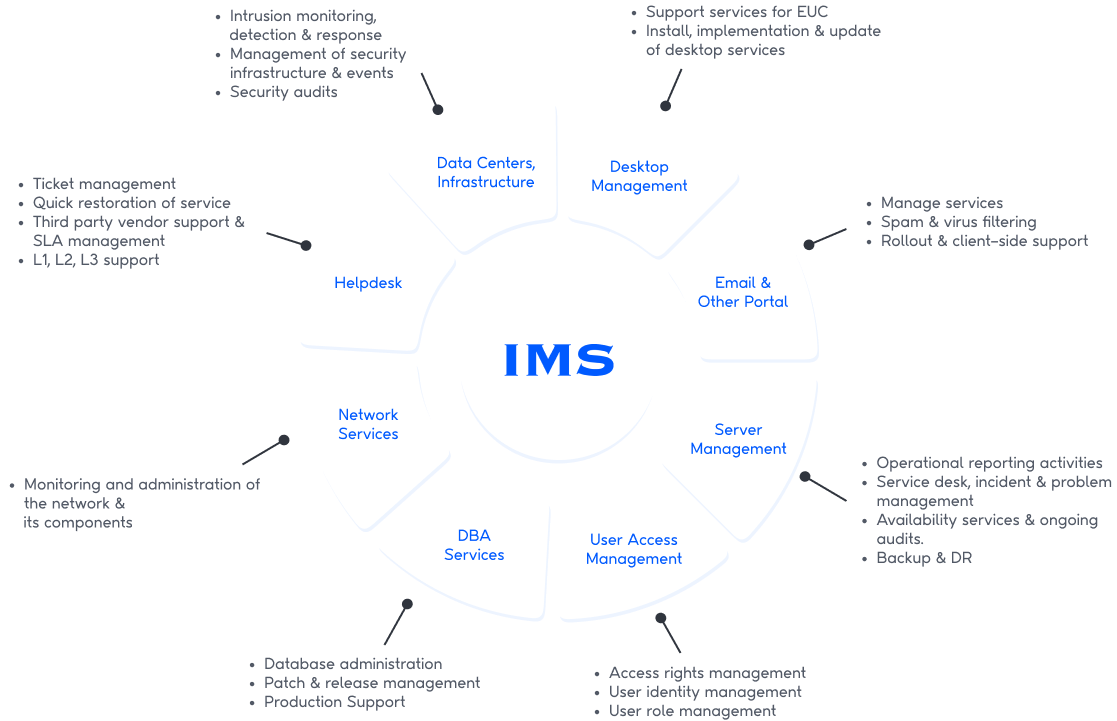
Our services include:
Systems Management
Thareja provides end-to-end systems management to ensure that your IT infrastructure operates efficiently and reliably. We handle everything from system monitoring to performance tuning and proactive maintenance, reducing the risk of downtime and service interruptions.
Facilities Management
Our facilities management services ensure that your physical infrastructure, including data centers and hardware, are managed effectively. We provide a full range of services, including power, cooling, and environmental controls, to maintain optimal operating conditions.
Systems Administration
Thareja systems administration services include the day-to-day management of servers, networks, and databases. Our team ensures that your IT systems are configured and maintained correctly, providing the reliability and security your business needs to thrive.
Cloud Services
Thareja offers a full range of cloud services to help businesses transition to more flexible, scalable, and cost-effective cloud environments. Whether you're migrating existing systems to the cloud, building cloud-native applications, or optimizing your current cloud infrastructure, Thareja cloud services are designed to enhance performance and reduce operating costs.
Security Services
With cybersecurity threats on the rise, security services are an essential component of any infrastructure management plan. Thareja provides advanced security solutions to protect your IT environment from evolving threats, ensuring your data and systems are secure, compliant with regulations, and resilient against breaches.
Support Services
Support services from Thareja include proactive system monitoring, troubleshooting, and technical support to ensure the smooth operation of your infrastructure. Our team is available around the clock to address any issues that arise, minimizing downtime and ensuring continuity.
Benefits of Thareja Infrastructure Services
Partnering with Thareja for infrastructure services enables businesses to achieve a wide range of operational benefits, including:
- Reduced Operating Costs: Thareja managed services allow businesses to cut costs by optimizing infrastructure efficiency and reducing the need for in-house teams to handle routine maintenance and management.
- Improved Operational Quality: With our ISO-certified processes, we ensure that your infrastructure operates at peak performance, delivering higher quality services to your customers and users.
- Increased Service Levels: Thareja proactive approach to infrastructure management ensures that service levels are consistently met or exceeded, improving customer satisfaction and business outcomes.
- Continuous Improvement in Systems Performance: We continually monitor and fine-tune your infrastructure to improve performance over time, ensuring that your systems are always running at their best.
- Enhanced Productivity: By allowing your internal teams to focus on strategic initiatives rather than day-to-day infrastructure management, Thareja helps improve productivity and drive innovation within your organization.
Additional Services to Support Your Digital Transformation
In addition to infrastructure services, Thareja provides a comprehensive range of digital transformation solutions to ensure that your business stays ahead in the digital age. Our services include:
- Cloud Migration and Optimization
- AI and Machine Learning Integration
- Robotic Process Automation (RPA)
- Big Data Analytics
- Cybersecurity Solutions
- Application Development and Maintenance
Partner with Thareja to Make Your Infrastructure Future-Ready
Thareja infrastructure services are designed to help businesses build, manage, and optimize the IT systems they need to support their digital transformation initiatives. Whether you’re upgrading existing infrastructure or implementing new technologies, our team of experts is ready to ensure your systems are resilient, scalable, and secure.
IT Security Best Practices for Remote and Hybrid Workforces
The pandemic transformed our lives, especially the way we work. Traditionally, employers believed that office workers needed to be physically present at their workplace to be most productive. With the world under lockdown, the concept of remote work became a necessity. While some companies had the technology, security systems and processes in place to manage this shift, many were caught unprepared and forced to rush in processes and systems to support remote workers, sometimes prioritizing speed of deployment over security.
After having worked remotely, many workers do not want to return to a fulltime office setting. According to a McKinsey survey, 63% of workers worldwide prefer flexible or remote working conditions, and more than 30% are willing to quit their current job if required to go back to an office fulltime. With a clear employee preference toward remote or hybrid work, employers have no choice but to offer flexible working models or face large-scale employee attrition.
Fortunately, hybrid work models also have an upside for employers. In addition to contributing to improved employee satisfaction and retention, employers are seeing reduced costs associated with decreased demand for office space and bandwidth. As such the business case for hybrid work models has never been stronger.
Embracing hybrid work models requires a thoughtful approach. Remote workers can expose your infrastructure and data to vulnerabilities which previously may have been a lesser concern. The good news is a combination of technology, policies and training can mitigate these risks.
Here are eight security best practices for remote and hybrid workforces:
Shared Responsibility Model: Hybrid workers need to understand that cloud security is a shared responsibility. This framework clearly defines users’ and administrators’ responsibilities and obligations when it comes to maintaining cloud security and supports them to fulfill their responsibilities.
Encryption: Robust encryption of data in transit, in use, and at rest is essential. Tools like Software Defined Wide Area Networks (SD-WAN) can be deployed to create a dynamic, multipoint VPN using IP security, to create encrypted tunnels for data transmission between remote users and corporate infrastructure, through the Internet. As a rule, all data should be encrypted before it is transmitted. For data at rest, all modern devices which store, or cache data can encrypt data.
Robust Passwords: Enforce the adoption of password best practices. This should include minimum standards on length, types of characters, and use of symbols. The generally accepted standard for strong passwords is to include at least 12 characters that must include uppercase and lowercase letters, numbers, and special characters.
Multi-Factor Authentication (MFA): Multi-factor authentication provides an additional layer of data security beyond a username and password. MFA can take several forms such as a PIN sent to a trusted device, a security key which the workers retain in their possession, personal history questions, or biometrics such as voice, or fingerprints.
Zero Trust: Traditional security models operate on the principle that once a user is authenticated, either by being in a secure corporate perimeter or by VPN, they are granted access to all resources authorized with their account. A Zero Trust posture assumes every user is a potential threat and includes authentication of devices and their integrity before granting access to each resource or zone within a corporate IT environment.
Data Categorization: This involves categorizing enterprise data based on its sensitivity and implementing a hierarchy of controls based on that sensitivity. This should not only include access controls, but consideration of how sensitive data is transmitted and stored. Servers, data centers, network attached storage and user devices can all cache data transferred through them. As such data categorization should include appropriate data destruction processes to ensure sensitive data is not on systems that lack adequate security policies and controls
Automation: Cloud Security Posture tools automate many aspects of security monitoring and incidence response. Security patches and updates should be automated across all enterprise infrastructure, systems, and user devices to the fullest extent possible. Critical security updates should not be delayed because of the lack of availability of IT resources, or by workers who prioritize their own work over updating the security apps on their devices.
Training, Policies, and Procedures: Remote workers face a wide range of security threats which are much less of a concern when they are within a secure corporate office. In addition to reinforcing IT security best practices, organizations need to consider situational issues such as securing devices and documents, preventing eavesdropping on conversations and computer screens, and other risks.
Thareja offers a full range of enterprise security services to help clients protect their sensitive data.
8 Cybersecurity Trends to Watch
The cybersecurity threat and management landscape is constantly changing. With the rise of remote workforces, cloud computing, and other Internet-based technologies, the number of potential targets for hackers has vastly expanded. As businesses continue to adopt new technologies and operating models, here are 8 cybersecurity trends you will be hearing more and more about:
IoT Security - It is estimated that there are 14.4 billion IoT devices in use around the world. But in this State of IoT 2022 report forecasted that by the year 2025, we’ll have 27 billion. With the rise in this new technology and connectivity to the Internet, the scope for threats is on the rise.
While device engineers and solution designers continuously seek new ways to secure IoT systems, organizations must continue to remain vigilant and adhere to best practices such as employee security awareness, strong passwords, dedicated wi-fi networks, encrypted wi-fi, modern firewalls, automated security patching, and other measures. Organizations will have to pay close attention to IoT system security because any weaknesses could result in a hacker disabling critical public or corporate infrastructure.
Ransomware Attacks - Ransomware is a constant threat. The Statista report Company Threat Outlooks predicted that ransomware attacks would be one of the top IT threats facing organizations in 2022. A simple email that looks completely genuine to an employee could trigger an extended period of chaos that compromises an organizations data and critical technology. In order to prevent these attacks, your employees need to be trained to spot these emails and security software needs to be continuously updated to identify and defend against the latest threats. This type of threat is expected to be an ongoing challenge for the foreseeable future.
Supply Chain Attacks - Hackers are not just targeting corporate infrastructure and data, they are trying to infiltrate the IT supply chain to create vulnerabilities in the source code of tools and technologies that are the foundation of networks and software applications.
Fifteen percent of organizations worldwide experienced Supply Chain Attacks in 2021. A recent Gartner prediction suggests that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains. Hacks like those seen against SolarWinds, Kaseya and GitLab will only become more common.
A successful hack of a corporate network mostly impacts that one entity. A successful hack of the technology supply chain can have an exponential impact introducing vulnerabilities into technology systems used by hundreds if not thousands of organizations who use that technology. Organizations that produce software and technology which is broadly used across the technology landscape need to recognize the threat hackers pose and remain vigilant for potential threats.
Cloud Security - With enterprises embracing Cloud computing for the many benefits it provides, the potential cost of a poorly planned cloud migration has never been higher. While leading cloud providers offer robust security, authentication and encryption solutions, many do not. Furthermore, improperly configured multi-tenant cloud solutions can allow hackers to access your confidential information without ever having to navigate your corporate security environment. Even seemingly secure cloud hosting solutions can be compromised by a lapse in judgment by an end user. As such, enhancing cloud security will be an ongoing priority for the foreseeable future.
Mobile Device Security - Mobile devices have become an indispensable part of our daily lives. Nearly two-thirds of people on earth own and use smartphones, storing many types of confidential information ranging from banking and credit card numbers, to personal medical information, to passcodes for corporate multifactor authentication. Because of the information stored on them, mobile devices are an appealing target for hackers. Measures to improve the security of these devices, both from an enterprise and from a personal standpoint, will become a growing priority in the future.
5G Internet - L5G offers tremendous advantages in terms of enabling remote workers to quickly access network resources to improve productivity. 5G by its fundamental nature is not secure. Data packets are transmitted across shared bandwidth to eventually reach their destination. Without rigorous security and encryption, data packets could be accessed and exploited by third parties for malicious purposes.
5G offers tremendous advantages in terms of enabling remote workers to quickly access network resources to improve productivity. 5G by its fundamental nature is not secure. Data packets are transmitted across shared bandwidth to eventually reach their destination. Without rigorous security and encryption, data packets could be accessed and exploited by third parties for malicious purposes.
Cybersecurity Mesh Architecture(CSMA) - With today’s remote and hybrid workforces, the number of security vulnerabilities organizations face has never been greater. To help manage these threats, Gartner established the concept of a cybersecurity mesh architecture (CSMA). The concept essentially involves layering complementary tools, technology, software and policies to secure every point of an enterprise’s network, both within its security perimeter, and for dispersed workers. By incorporating modern tools and techniques, CSMA empowers a zero trust approach to network and infrastructure security which enforces credentialing at every access point within an enterprise network.
Awareness - Cyber-attacks are often the result of human error, rather than a flaw in the digital security ecosystem. Training and ongoing awareness measures to establish and reinforce behaviors that promote cybersecurity will become increasingly common. Progressive businesses are making investments in comprehensive initiatives to alter user behavior to enhance the overall security of their enterprise systems.
Cybersecurity is more crucial than ever. It is no longer just a technology risk, it is a business risk. To learn more about how Thareja cybersecurity services team can help secure your data and technology infrastructure.
Choose the Right IT Support Partner
Many companies today are struggling to find the IT resources they need to manage their technology infrastructure. This combined with the escalating costs, has led many to consider outsourcing IT support to an outside supplier. Finding the right IT support partner for your business can be challenging. Here are seven factors to consider when choosing an IT support supplier:
Experience
The first factor to assess when evaluating potential IT support partners should be their skills and experience with your technology stack. The supplier should be able to not only identify team members who possess skills and certifications related to the technologies you use but should be able to demonstrate a track record of success support clients with a similar technology ecosystem.
It is also important to consider the size of the supplier’s team. Issues can arise at any time. A potential supplier should not only have qualified professionals available during business hours but have a bench that can provide support whenever it is needed.
Industry Certifications and Expertise
Organizations that possess industry recognized certifications have incorporated best practices into their processes and procedures. Before being awarded a certification, the supplier would have been required to complete an audit to demonstrate their adherence to the standards that are part of the certification. As certifications are easy to verify, they can serve as a quick way to assess the credibility of a potential IT support partner.
Organizations that possess industry recognized certifications have incorporated best practices into their processes and procedures. Before being awarded a certification, the supplier would have been required to complete an audit to demonstrate their adherence to the standards that are part of the certification. As certifications are easy to verify, they can serve as a quick way to assess the credibility of a potential IT support partner.
Service Levels & Quality
Your IT support should always be readily available to help you whenever an issue arises that needs attention. Service level specifications should be specific and detailed setting timeframes for supplier acknowledgement and resolution of issues, based on the level of support required. Part of these specifications should be clear criteria for escalation, and a communications plan to ensure you remain fully informed should an issue arise.
Another important feature to look for is the use of a ticketing system. Ticketing systems allow you and the supplier to track all service requests and document them through to completion. The added benefit of ticketing systems is that they can be a valuable source of information when evaluating the supplier’s performance.
Be sure to inquire about any quality assurance and customer satisfaction programs the supplier has in place. Formal processes for post-mortem reviews of incident response can contribute to improved service delivery over time. Customer satisfaction initiatives can also lead to process improvements that allow the supplier to better meet your needs over time.
Scope of Services & Flexibility
When evaluating potential IT support partners, it is important to not just focus on the specific services you immediately need. Your initial plan for IT support might begin with a modest, well-defined requirement. As the needs of your business change, you may choose to outsource additional support functions, or possibly management of your entire technology ecosystem.
An established working relationship with a capable vendor who offers a broad range of additional services, allows you to quickly and efficiently outsource additional activities should the need arise. Beyond making it easier to outsource additional services at a lower cost, a versatile vendor will also allow you to maintain a single, point of accountability for all your outsourced IT support services.
Having a vendor who cannot adapt to meet your future requirements will likely result in you having to transition your IT support needs to a new vendor creating operating hassles for you, and a learning curve for the new vendor.
Having a vendor who cannot adapt to meet your future requirements will likely result in you having to transition your IT support needs to a new vendor creating operating hassles for you, and a learning curve for the new vendor.
Security
Outsourced IT support services are often partially or entirely performed by remote workers. As such, security should always be a paramount consideration when outsourcing. The vendor should have a robust security plan that demonstrates includes the technologies and processes needed to protect your systems and data. Furthermore, that security plan should be compliant with any regulatory and industry standards or best practices that apply to your business. Depending on your industry, you may also require vendor staff possess active security clearances or undergo background investigations.
Transparency
A good IT support vendor will allow you to have virtually complete visibility into their service delivery and the performance of your systems. This should include several components:
- Dashboards to allow you to view real-time performance of your systems,
- A clear team structure identifying individuals, their roles and their responsibilities,
- Tiered contact plan and formal issue escalation process,
- A clear explanation of what services are included in your services agreement and what is not,
- Demonstrated culture of honesty and integrity,
- A willingness to explain issues to your satisfaction, and
- Including you in key decisions, should you wish.
Pricing
Most companies find that outsourcing IT support functions saves them money. To ensure a positive financial outcome of your outsourced IT support initiative, here are some important considerations:
- Scrutinize the services that are covered by the vendor proposal and which activities will incur additional costs.
- If a vendor is offering bundled services, consider whether the individual services in the package align with your needs and represent good value for you.
- Are there services you need, or service level specifications you require, which are beyond the scope of the proposal being offered?
- Is there a mechanism for you to control or approve incremental charges?
Thareja IT support services can allow organizations to reduce costs, improve management of IT systems, better support end users, and increase their focus on their core business.
Thareja Managed Services & Support
Thareja has delivered Managed Services engagements, including many large scale and complex engagements, across more than 18 countries globally. We have the established infrastructure, resources, and methodologies needed to ensure a successful transition and ongoing operations. Thareja managed services expertise comes from handling mission-critical business functions for multi-national clients with demanding SLA standards.
Thareja managed services offering includes the following domains:
Application Management & Support
Thareja helps clients to ensure their critical business applications are performing optimally and evolving to meet their changing business needs. Thareja manages application updates, enhancements, regulatory compliance, performance optimization, and support to free up client resources and reduce costs.
Deployment Management Services
Thareja helps clients to plan, test, and implement mass application deployments. With Thareja on your team, you can rest assured that potential risks have been identified and addressed, process inefficiencies have been corrected, and a thorough testing plan has been put in place to ensure smooth mass deployments.
Infrastructure Management and Support
Thareja helps clients better manage their critical IT infrastructure with remote and onsite management and support services. Whether it is end-to-end outsourced datacenter management or task-specific services, Thareja has the qualified resources and procedures needed to make your outsourcing strategy a success.
Data Analytics Outsourcing
Thareja Analytics Outsourcing allows clients harness their Big Data to inform better and faster decision-making. Our Analytics Outsourcing services allow clients to benefit from world class data storage, management, machine learning and reporting services.
IT Staffing Managed Services
Thareja IT Staffing Managed Services allows clients to support the varied IT requirements across their organizations within a structured policy and procedure framework that ensures regulatory compliance and cost savings. Thareja offers clients the processes, personal expertise, and technology needed to make their program a success.
Training & Development
We leverage technology to help clients elevate the knowledge and skills of their dispersed workforces to achieve improved business results. From needs assessments to platform selection and deployment, through to ongoing maintenance and support, Thareja team of advisors can guide you every step of the way.
Thareja Enterprise Security Services
Thareja works with clients to establish and maintain a secure business environment for data by deploying comprehensive, business-aligned, enterprise security architectures enabled by people, processes, and technology to minimize risks and lower costs.
Thareja enterprise security services include:
Advisory Services
- Security Strategy & Roadmap
- Enterprise/Cloud Security Architecture
- Regulatory Impact Assessments
- CISO-on-Demand / Shared CISO
Information Security
- Adaptive End-Point Protection with EDR
- Mobile Security Management (Application - M&M Device – MDM)
- Identity & Privilege Management
- Data Protection & Rights Management (DLP/DRM/IRM)
Assurance Services
- Security Risk & Privacy Assessments
- Vulnerability/Penetration Assessments
- Application Testing/Secure Code Reviews
- Phishing/Security Awareness Testing
- Legacy Technology Effectiveness Assessment
Threat Detection and Response
- 24/7/365 SOC Services
- Perpetual Threat Monitoring
- User & Entity Behavior Analysis (UEBA)
- Threat Hunting
- Security Orchestration, Automation & Response (SOAR)
- SOC Capability & Maturity Assessment
Helping the ambitious achieve more.
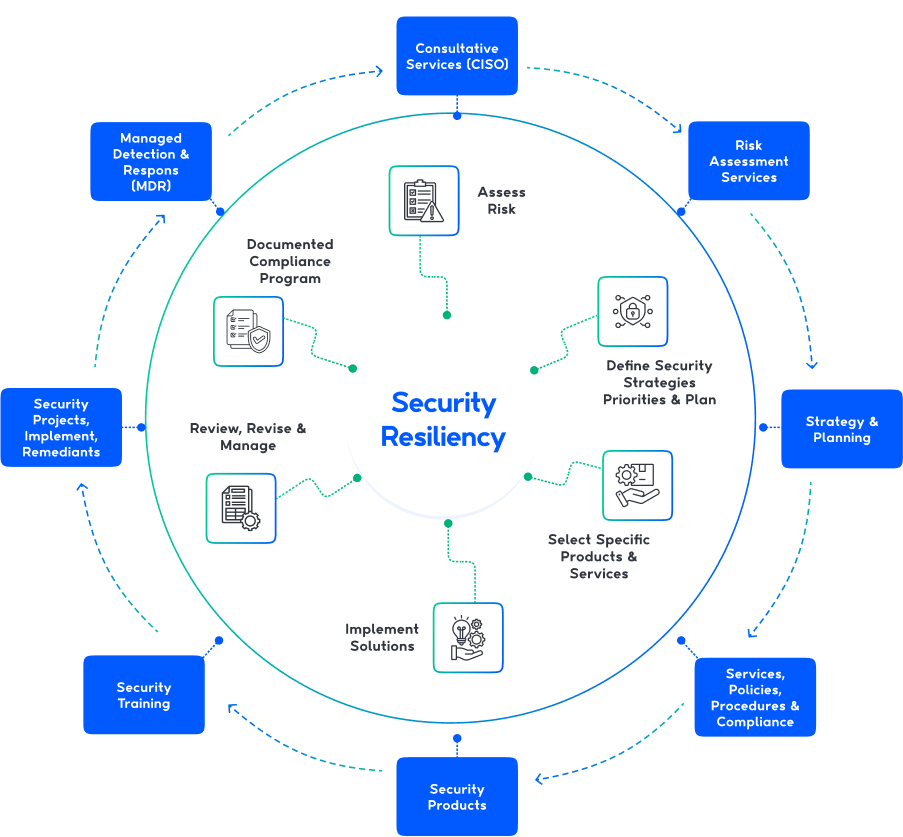
Thareja Enterprise Security Services can be delivered via onsite, remote and hybrid engagement models.
For more information about Thareja Infrastructure Services, Contact Us.
About Our Services
The key to your success?
Our embedded talent model.
Thareja AI wants to democratize Global HR Ops.
We are combining AI-driven recruiting, proof-of-work analytics, and global payroll compliance into one seamless platform. Instead of sifting through thousands of candidates, we deliver pre-vetted, high-quality talent with AI-generated reports alongside timesheets—so you can see actual output, not just hours worked.
We don’t just replace recruiters—we eliminate the outdated hiring model, from hiring to payments, at a fraction of the cost.
Compare packages
Dedicated Resource
Global Wizards
Elite Tech / Marketing talent from USA or India
Flexible Full Stack
Growth Agency Membership
Access to 130+ Talented Creative & Technology Specialists
Your Own Talent
Employer of Record
Can be your Employer of Record in 65+ countries
FAQ
How does proof of work actually work?
Because your remote team isn't paid to scroll instagram, you only pay for time spent on when your talent is actually doing your work. We monitor your talent with time trackers, screenshot monitors and what apps & URLs they visit.
Are there any refunds if I don't like the service?
We can return your money for the days that are left due to the cancelation of your subscription. Due to the high-quality nature of the work, there will be no refunds issued for work that was already done or for the days before your cancelation request was received.
Who are the designers or technologists?
For the 30-50% of 1 in-house designer, you get a dedicated team of senior designers, developers, and technologists with over 5 years of proven experience. This means you�ll work with multiple designers and technologists at the same time which helps you close 60% more tasks quicker. Also, power-up requests such as animations or custom illustrations are provided by either our professional specialist or partner designers.
This service is offered by Top 1% of Talent
- Hand-picked Global Wizard
- High-quality work
- Experienced with all sizes of businesses
- Dedicated Resource
- Growth Agency Membership
- Employer of Record
Global Wizards
Starting at $2,995/monthHire Elite Tech / Marketing talent from USA or India
-
Top Global Talent
-
Employee Payroll & Tax management
-
Save 70% Labor Cost
-
IC compliance and secure IP
-
Time tracking & Proof of Work (Thareja AI)
Flexible Full Stack
Starting at $4,995/monthAccess to 130+ Talented Creative & Technology Specialists
-
Top Global Talent
-
Employee Payroll & Tax management
-
Save 70% Labor Cost
-
IC compliance and secure IP
-
Time tracking & Proof of Work (Thareja AI)
Your Own Talent
Starting at $199/monthAdd us as Employer of Record in 65+ countries
-
Top Global Talent
-
Employee Payroll & Tax management
-
Save 70% Labor Cost
-
IC compliance and secure IP
-
Time tracking & Proof of Work (Thareja AI)
Global Operations
Our mission is to empower professionals to thrive and deliver exceptional work—anytime, anywhere.
4.9 Stars
Google Reviews
Everything we do, we do it for our users. We care about product quality, attention to detail, and making a positive impact on as many people as we can.
600K+
Downloads
Hundreds of thousands of users around the world downloaded our 9+ apps.
Thareja AI has been used to deliver exceptional services for top brands around the world.
